Besides doing (traditional) dot1X on the wired switchport on which a access-point is connected, it is also possible to let the wireless controller authorize access-points within the join process. This post gives the necessary configuration for the use of a external AAA RADIUS server (ISE) within this process for AirOS and IOS-XE wireless controllers.
1. AirOS
(2504) >config radius auth add 1 192.168.208.51 1812 ascii Pr3sh@r3dk3y
(2504) >config radius auth network 1 enable
(2504) >config macfilter radius-compat cisco
(2504) >config auth-list ap-policy authorize-ap username ap-mac
(2504) >config auth-list ap-policy authorize-ap enable
2. IOS-XE
CAT1(config)#aaa new-model
CAT1(config)#radius server AAA-RADIUS-ISE01
CAT1(config-radius-server)#address ipv4 192.168.208.51 auth-port 1812 acct-port 1813
CAT1(config-radius-server)#key 0 Pr3sh@r3dk3y
CAT1(config)#aaa group server radius AAA-GRP-ISE
CAT1(config-sg-radius)#server name AAA-RADIUS-ISE01
CAT1(config-sg-radius)#subscriber mac-filtering security-mode mac
CAT1(config)#ap auth-list ap-policy authorize-ap
CAT1(config)#aaa authorization network default group AAA-GRP-ISE
3. ISE
While I was performing some testing there where two things which caught my attention on the ISE logging:
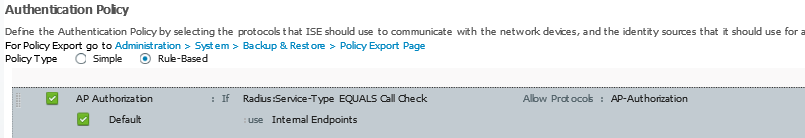
1) By default IOS-XE will send a blank password which ISE does not understand (fix for this is the “subscriber mac-filtering security-mode mac” command)
2) In ISE the AirOS authentication requests showed up as MAB method, while the requests from IOS-XE used the PAP_ASCII method. Despite some research I was unable to find a way to change this on the IOS-XE side. I ended up with the following configuration to support both platforms within the same set of rules:
Allowed protocols

Authentication policy
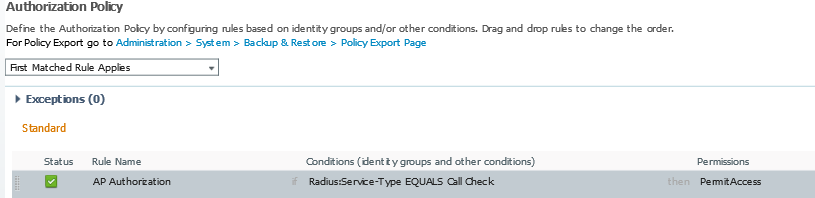
Authorization policy
Last month I deployed a remote access VPN solution based on Cisco IOS routers with webvpn and Cisco’s AnyConnect client. After some basic tests everything looked good until someone with Windows 8.1 tried to make a connection. The user complained that it took at least 20 seconds before the authentication prompt appeared after making the initial connection. And guess what, the user was right! It was even worse -> also Android and iOS showed the same behavior.
So we fired up wireshark and looked at the packets to see what was going. We discovered that AnyConnect sends a client hello message using TLS 1.2, the IOS routers send a [FIN, ACK], terminating the session. AnyConnect eventually tries to connect using TLS 1.0, but that process took over 20 seconds to complete. So I contacted TAC and they filled a bug for this case (CSCun89616).
The good news is that Cisco fixed this bug with creating a new software release. The bad news is that at the this very moment there is not a software release out where bug CSCun89616 is fixed and the router does not crash when using webvpn because of bug CSCug17485… 🙁
So to make a long story short; if you are running into this issue you can’t fix it without giving up stability. I’m still in contact with TAC, so when there is a stable release where both bugs are fixed, I will update this post.
Update may: In IOS versions 15.3(3)M3 and 15.4(3)M both bugs should be fixed.
Working with certificates time to time can be a little difficult, implementations differ and there are more than one certificate “formats”. This is also the case when it comes to importing a “pfx” archive to Cisco Prime Infrastructure (1.x or 2.x). If you search the web you will find a lot topics, but you will have to mix those together to get the job really done.
In this scenario you have a wildcard certificate and the private key combined together in a pfx archive (cert.pfx). You will need a openssl installation, the CA bundle (Root certificate and intermediates certificates, “CA-CERTS.CER”) which you can download from the certificate authorities website and these six steps:
1. Export the pfx archive to a standalone certificate and private key
openssl pkcs12 -in cert.pfx -nocerts -out key.pem
openssl pkcs12 -in cert.pfx -clcerts -nokeys -out cert.pem
2. Decrypt the private key
openssl rsa -in key.pem -out key2.pem
3. Convert certificate from pem to der format
openssl x509 -outform der -in cert.pem -out cert.der
4. Download the “CA-CERTS.CER”, “key2.pem” and “cert.der” files with FTP from the Prime CLI
5. Import the CA certs in Prime:
PRIME/admin# ncs key importcacert CA-CERTS CA-CERTS.cer repository defaultRepo
INFO: no staging url defined, using local space. rval:2
truststore used is /opt/CSCOlumos/conf/truststore
The NCS server is running
Changes will take affect on the next server restart
Importing certificate to trust store
6. Import certificate and private key
PRIME/admin# ncs key importkey key2.pem cert.der repository defaultRepo
INFO: no staging url defined, using local space. rval:2
INFO: no staging url defined, using local space. rval:2
truststore used is /opt/CSCOlumos/conf/truststore
The NCS server is running
Changes will take affect on the next server restart
Importing RSA key and matching certificate
7. Restart the NCS application, and drink a cup of coffee.. 😉
PRIME/admin# ncs stop
PRIME/admin# ncs start
Most Cisco AnyConnect VPN configurations I see in the field, or have deployment myself, are terminated on a Cisco ASA firewall who is directly connected to the internet. However, in some bigger networks it is not uncommon to have another firewall in front of the remote access / VPN block in your network or to have an access-list on the routers in the internet edge.
Everybody knows the story about the biggest pro which the Cisco AnyConnect solution has if you compare it to the old IPSEC remote access based solution –> “it just works everywhere™”. That story is based on the fact that in most guest and mobile networks SSL network traffic (TCP/443) is allowed. This is true; AnyConnect will work fine if DNS is working and TCP port 443 is open. However, AnyConnect will try to use the DTLS protocol first which uses UDP port 443, if it fails than the client will fall back to use SSL for the transport of user data. The reason that AnyConnect prefers DTLS is that DTLS has less delay because of the connectionless nature of UDP and thus performance is better then with a SSL tunnel.
It is very easy to check if you are actually using DTLS in the AnyConnect client:
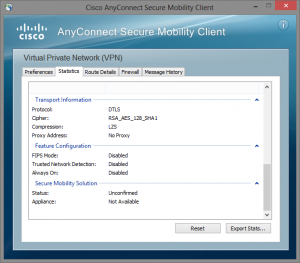 Conclusion:
Conclusion:
If you filter the network traffic destinate to a Cisco IOS webvpn router or Cisco ASA firewall in the remote access / VPN block in your network don’t forget to open UDP port 443 also.. 🙂
With Cisco ASA’s you can open HTTP network traffic so you can inspect it and even block websites if you want to. Remember that this only works for non-encrypted traffic, if you want to inspect encrypted traffic you gonna need a solution where you can do a MITM (Man In The Middle) attack.
Here you have a very simple example where the dutch website “autoblog.nl” is being blocked for clients in VLAN 10 with a IPv4 address in the 192.168.10.0/24 network.
regex URL-AUTOBLOG.NL ".autoblog.nl"
access-list ACL-CMAP-VLAN10-HTTP extended permit tcp 192.168.10.0 255.255.255.0 any eq www
class-map type regex match-any CMAP-REGEX-HTTP
match regex URL-AUTOBLOG.NL
class-map CMAP-VLAN10-HTTP
match access-list ACL-CMAP-VLAN10-HTTP
policy-map type inspect http PMAP-VLAN10-HTTP
parameters
match request header host regex class CMAP-REGEX-HTTP
reset log
service-policy PMAP-VLAN10 interface VLAN10
CCIE #53532, Frisian, curious, workaholic, wireless, security and more!



