This weekend I was able to make the time (and got the required service window 🙂 ) to migrate the home Wi-Fi network from AireOS 8.5.161.0 towards a new vWLC based on AireOS 8.10.121.0. In this post I list the things that stood out for me with the new software.
Security:
– Specifying the AP username and password is now part of the installation wizard. In case you upgrade an existing installation and haven’t configured this account, you will no longer have console access with the default credentials once the AP has joined the controller.
– The default (and thus very insecure) SNMP settings are removed.
Interface:
– The SSH login “doesn’t ask twice” for an username anymore (Note: changed since AireOS 8.6).
– When an AP is in downloading status, you now see the IP address of the AP in the GUI.
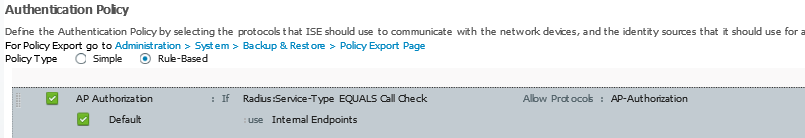
– The level of access the logged-in user has, is now being displayed in the GUI:

– To make the “Authentication Key Management” list with all the check boxes more intuitive, you now have to specify if your WLAN is a “Enterprise” or “Personal” one:

– A new section has come up under the security tab of the WLAN called “RADIUS Authentication Survivability”. During the writing of this post I was unable to find documentation regarding this feature, but if the name implies what it does it might be worth the effort to create another post dedicated to this feature 🙂

– AP (group) NTP server settings in the GUI.
– “Assisted Roaming Prediction Optimization” (e.q. 802.11k for non 802.11k clients) has made it back on the GUI after being removed in 8.5.
(Note: you don’t want this feature enabled, especially when you have to support Android clients.)
Changed default settings:
– “Flexconnect Arp-Cache” is now enabled by default.
– When you create a WLAN, the “Over the DS functionality” part of the 802.11r configuration, is now disabled by default.
– The “fast-ssid-change” feature is now enabled by default. (Note: this setting doesn’t exists on the new IOS-XE based Catalyst 9800 wireless controllers anymore since it is the default behavior for this platform anyway.)
Despite that the AireOS based platforms are almost at the end of there era, it is good to see some long awaited changes/features are being implemented. Check for additional information the corresponding release notes and the AireOS Feature List Per Release document.